Understanding Business Email Compromise (BEC): What It Is and How It Works

Business email compromise (BEC) is becoming an increasingly serious threat for small and medium-sized businesses (SMBs)—and it’s easy to see why.
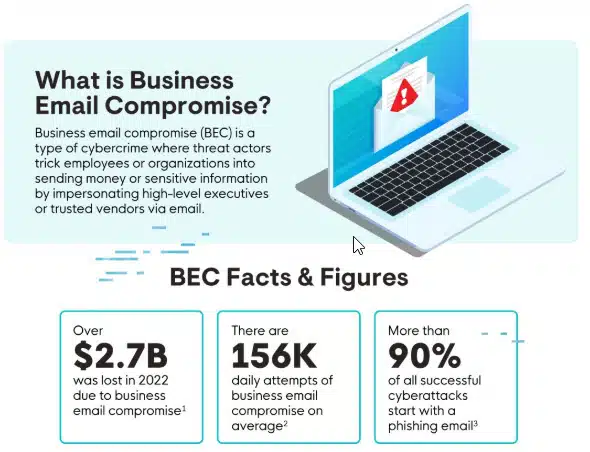
In 2022 alone, BEC attacks caused a staggering $2.7 billion in losses, marking a 12.5% jump from the previous year.
As these attacks continue to exploit inboxes and deceive businesses, organizations of all sizes must stay vigilant. Let’s break down what BEC is, how it works, and how businesses can protect themselves against these costly scams.
What Is Business Email Compromise?
Business email compromise (BEC) is a cyberattack that targets email accounts within an organization to carry out fraudulent activities such as wire fraud, phishing, and theft of sensitive data or credentials.
Attackers often impersonate high-ranking executives or trusted vendors through carefully crafted emails designed to deceive employees into transferring money or sharing confidential information. These schemes rely on social engineering tactics, making them both sophisticated and highly effective.
By understanding how BEC operates and implementing proactive defenses, businesses can significantly reduce their risk of falling victim to these increasingly common scams.
How Do BEC Attacks Work?
Business email compromise (BEC) attacks are highly strategic and often follow a calculated process:
- Research and Reconnaissance:
Attackers start by gathering information about their targets, including names, roles, and relationships within the organization. - Email Compromise or Account Takeover:
Threat actors gain access to an email account through phishing, social engineering, or exploiting software vulnerabilities. - Impersonation:
Once access is secured, attackers impersonate trusted individuals—such as a CEO, CFO, or vendor—by using either a spoofed or compromised email account. - Deception:
Using convincing emails, attackers trick employees into:- Transferring money.
- Sharing sensitive information.
- Downloading malicious attachments.
BEC attacks are notoriously hard to detect because they rely heavily on social engineering rather than technical exploits. Traditional security tools like spam filters often fail to catch them.
Common Examples of BEC Attacks
BEC scams come in various forms, but some of the most prevalent tactics include:
- Invoice Scams:
Attackers hijack a vendor’s email account and send fake invoices with altered payment details, directing funds to their own accounts. - CEO Fraud:
Impersonating a high-ranking executive, attackers send urgent requests for wire transfers, gift card purchases, or sensitive information, often targeting employees in finance or HR. - Payroll Diversion:
Posing as HR staff, attackers request changes to an employee’s direct deposit details, rerouting paychecks to fraudulent accounts.
How to Combat BEC Attacks
BEC attacks target human behavior, so defense strategies need to focus on empowering and protecting people. Here’s how SMBs can reduce their risk:
- Security Awareness Training:
- Regularly train employees to recognize phishing attempts and suspicious emails.
- Teach staff to verify unusual requests through alternate communication channels.
- Implement Multi-Factor Authentication (MFA):
- Add an extra layer of security to email accounts, requiring additional verification for login attempts.
- Adopt Managed Detection and Response (MDR):
- Use MDR tools to monitor for anomalies, such as suspicious login attempts or unusual email inbox rules.
- Establish Clear Policies:
- Require verbal confirmation for high-value transactions or sensitive data requests.
How Intech-Hawaii Can Help Prevent BEC Attacks
While BEC attacks are a growing threat, businesses don’t have to face them alone. Intech-Hawaii offers comprehensive solutions to help organizations safeguard against these costly scams by combining cutting-edge technology, strategic policies, and employee training. Here’s how Intech-Hawaii can help:
1. Comprehensive Security Training
Intech-Hawaii provides tailored cybersecurity awareness training to educate employees about the tactics used in BEC attacks.
- Employees learn to identify phishing emails, verify unusual requests, and respond appropriately to potential threats.
- Regular training sessions ensure that your team stays up to date on the latest scams and vulnerabilities.
2. Advanced Technology Solutions
Intech-Hawaii implements robust security tools to detect and block threats before they reach your inbox.
- Multi-Factor Authentication (MFA): Adds an extra layer of protection to email accounts, making it harder for attackers to gain unauthorized access.
- Managed Detection and Response (MDR): Proactively monitors your systems for unusual activity, such as suspicious login attempts or email rule changes, and takes action to neutralize threats.
Contact us today to find out how we can help your business safeguard itself from BEC attacks.




